国网北京电力建设研究院网站wordpress添加工具
照明系统设计者通常需要向客户提供IES格式的数据。照明工程学会 (Illuminating Engineering Society,IES) 文件格式便于传输辉度数据,该格式得到了制造商和设计师的广泛认可。本文描述了如何生成IES文件并验证结果。(联系我们获取文章附件)
简介
复杂的照明系统可以在OpticStudio的非序列模式下进行设计和优化,之后,您可能需要向潜在客户提供输出数据,以便他们能够评估系统性能,并在他们自己的应用程序中使用。可以使用IES文件格式导出这些数据。IES常用于照明行业,以描述光源和完整的照明系统。使用OpticStudio可轻易生成IES文件格式。
本文将演示如何将保存到光谱数据格式文件的光线转换为IES文件。
IES 文件格式
IES文件格式假设光源/照明系统距离观测平面足够远,可以将光源看作是没有空间变化的点光源,这使得IES文件比其他格式的文件小得多。另外,光谱数据不包含在IES文件中,如果需要的话,必须生成单独的文件来保存光谱数据。OpticStudio可以轻松处理转换,并直接生成IES数据。
要直接生成IES数据,只需使用极探测器(Polar Detector ) 探测光线,然后在非序列元件编辑器(Non-Sequential Component Editor)的“工具(Tools)”菜单下使用“导出极探测器数据作为光源文件(Export Polar Detector Data as Source File)”。有关详细信息,请参阅文章 "如何使用极探测器和IESNA/EULUMDAT光源数据"。
在OpticStudio中可以将光线数据库中的光线保存为 . SDF文件格式(光谱数据格式),该格式包含光线击中特定物体上一点的所有光线数据。该数据集可以简化为IES文件,通过点击:库(Libraries) > IES光源模型(IES Source Models) >将光源文件转换为IES(Convert Source File to IES),使用转换光源文件(Convert Source File)将其转换为IES格式。
通常会在退出系统时保存光线,然后将该光线集转换为IES文件提供给客户。在这两种情况下,都“分离”了与光源相关的空间数据,只显示了远场结构。
本文将重点介绍IES文件生成的第二种方法。
生成 SDF
本文附件中包含LED模型的示例文件,该模型包括对LED光源的简单描述(使用体光源(Source Volume)、矩形物体(Rectangle object)),以及表示物理结构(接触线、电极、模具和外壳)的几何物体,这些物理结构将包含在LED封装中。
要生成代表该光源模型的光谱颜色文件,需要将1000万束光线追迹到位于光源附近的矩形探测器(Detector Rectangle)物体上。在光线追迹期间,还应该选择保存光线(Save Rays)选项。
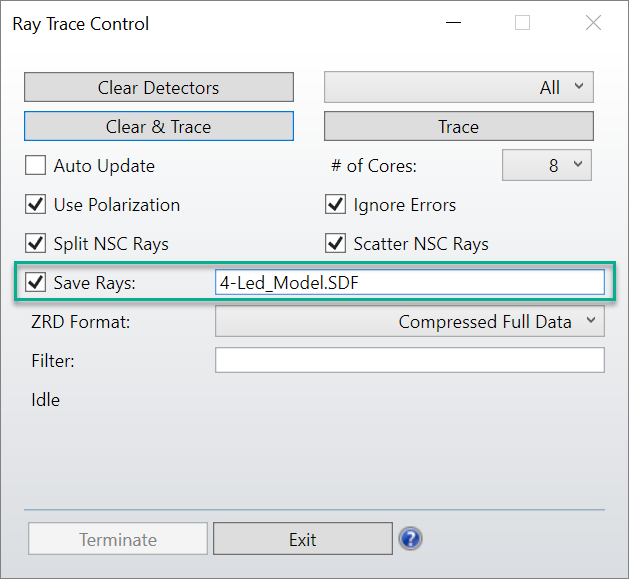
保存文件名的语法应该是 “ #-Name.SDF ”,其中 # 表示保存光线的探测器物体的编号(在示例中为物体 #4)。物体编号不会作为文件名的一部分保存;对于上述示例,生成的文件名为Led_Model.SDF。
请注意,上述方法并不局限于保存到达探测器上的光线。可以为在非序列模型中光线到达的任何物体生成SDF文件,只需在保存光线的输入中指定所需物体的编号作为文件名的第一部分。例如,如果希望将到达物体 #1上的光线保存到SDF文件中,那么在保存光线给出的输入文件名将以 “1-” 开始。
输入以上设置后,点击清空探测器 (Clear Detectors),然后进行光线追迹,并将在探测器上获得的结果保存到SDF文件中。将该文件放置在 {Zemax}\Objects\Sources\Source Files文件夹中(有关更多信息参阅帮助文件中“设置(Setup) 选项卡>系统组(System Group) > 配置选项(Project Preferences) >文件夹 (Folders)”参阅帮助文件)。
SDF文件可以通过文件光源(Source File) 物体用于任何OpticStudio非序列文件。关于文件光源物体的更多信息可以在帮助文件中通过点击:设置(Setup)选项卡>编辑器组(Editors Group) >非序列元件编辑器 (Non-Sequential Component Editor) > 非序列光源(Non-Sequential Sources)找到。
转换为IES文件
现在准备将SDF文件转换为IES文件,点击:库(Libraries) > IES光源模型 (IES Source Models),使用将光源文件转换为IES(Convert Source File to IES)。
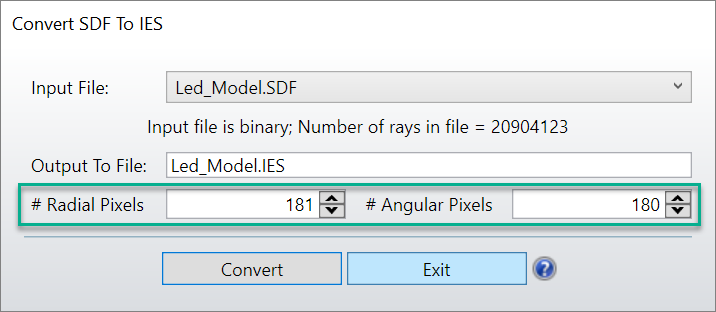
任何位于{Zemax}\Objects\Sources\Source Files文件夹中的SDF文件都可以使用该工具。此功能的关键输入是在生成的IES文件中指定垂直(径向)和水平(角度)像素的数量。像素数量越大,分辨率越高,但如果初始SDF中的光线数量较少,则会导致光线追迹结果出现不理想的峰或噪声。当转换包含大约100,000或更多光线的SDF文件时,默认的像素化值(垂直角度为181,水平角度为180)是合理的。请注意,虽然这个示例文件中发射了1000万束光线,但有2000多万束光线到达了探测器,并保存在SDF文件中。这是因为在光线追迹期间,选择了“分裂光线(Split Rays)”在系统中分裂光线能量。
虽然IES文件包含用于描述光源角分布的光度值(例如:坎德拉),但该文件不包含关于光源光谱分布的显性信息。为了确保SDF文件中包含的光谱信息在转换为IES时不会丢失,OpticStudio将在单独的光谱 ( SPCD ) 文件中保留这些信息。SPCD文件将与输出的IES文件具有相同的基本名称,只是使用不同的扩展名(SPCD)。有关光谱文件语法的更多细节,请参阅帮助文件,可通过点击:“设置选项卡(The Setup Tab ) >编辑器组(Editors Group)>非序列元件编辑器(Non-sequential Component Editor ) >物体属性(Object Properties) >光源 (Sources) > 定义光谱文件(Defining a spectrum file)”打开。
要将SDF文件转换为IES和 SPCD 文件,只需单击转换文件(Convert) 按钮。将转换后的IES文件放在{Zemax}\Objects\Sources\IESNA文件夹中,而转换后的SPCD文件将被放在{Zemax}\Objects\Sources\Spectrum Files文件夹中。
验证结果
为了验证转换结果,可以在配光曲线(Directivity Plot)或极坐标图(Polar Plot)中查看SDF和IES文件的远场分布(这两个功能都可以在分析(Analysis) >光源查看器(Source viewer) 菜单中找到)。例如,扫描角度为0、45和90度时,两个光源文件的半圆配光曲线比较如下:
SDF
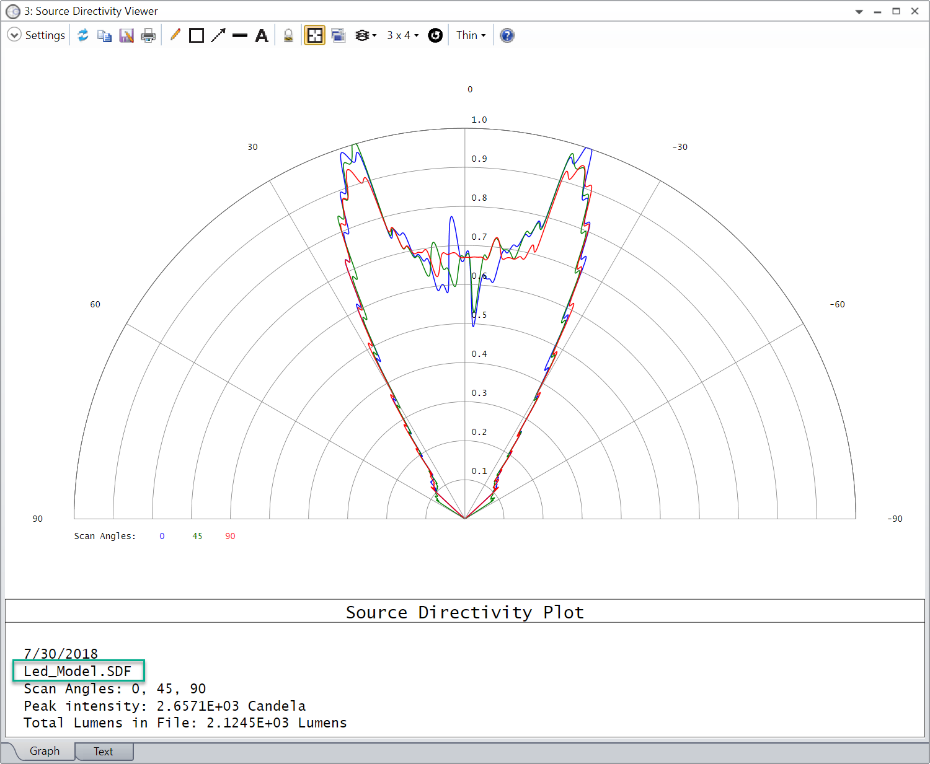
IES
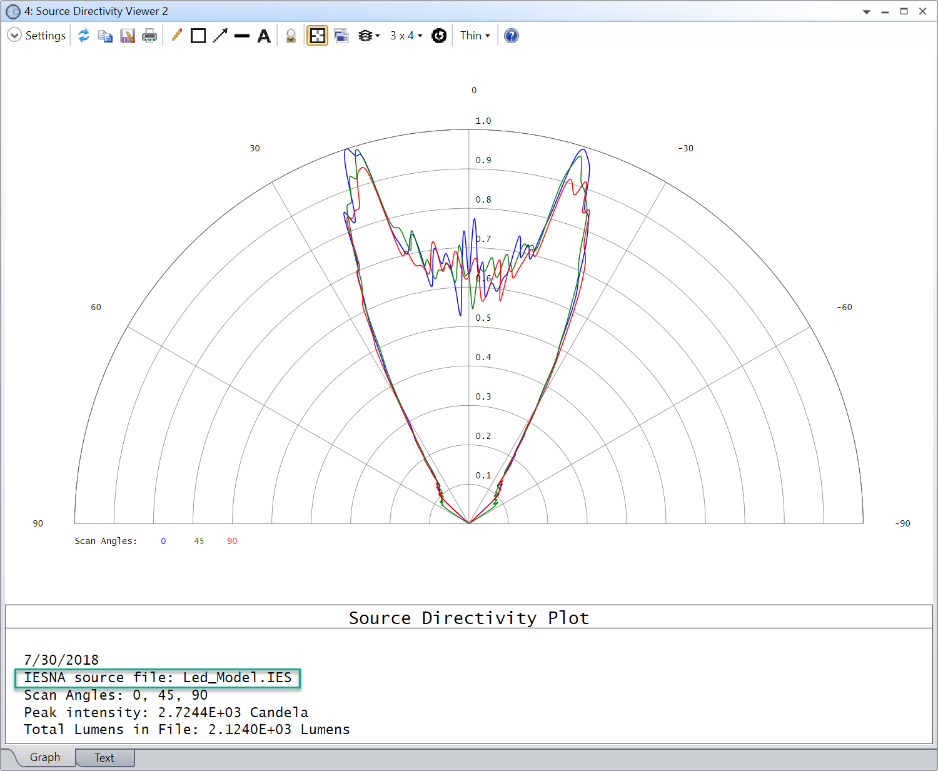
正如预期的那样,两个文件的结果几乎相同。通过降低转换期间IES文件中使用的像素数量,可以减少IES结果中相对于SDF结果的额外散点偏差。
将光源成像到远处平面上时,可以使用光源照度图(Source Illumination Map) (在分析(Analyze) >应用(Applications) > 光源照度图(Source Illumination Map)查看光源照度分布。就像配光曲线(和极坐标)图一样,照度图可以用于SDF或IES文件(所有这些分析也可以用于RSMX文件)。在使用IES文件时,通常需要指定SPCD文件来表示光源光谱分布:
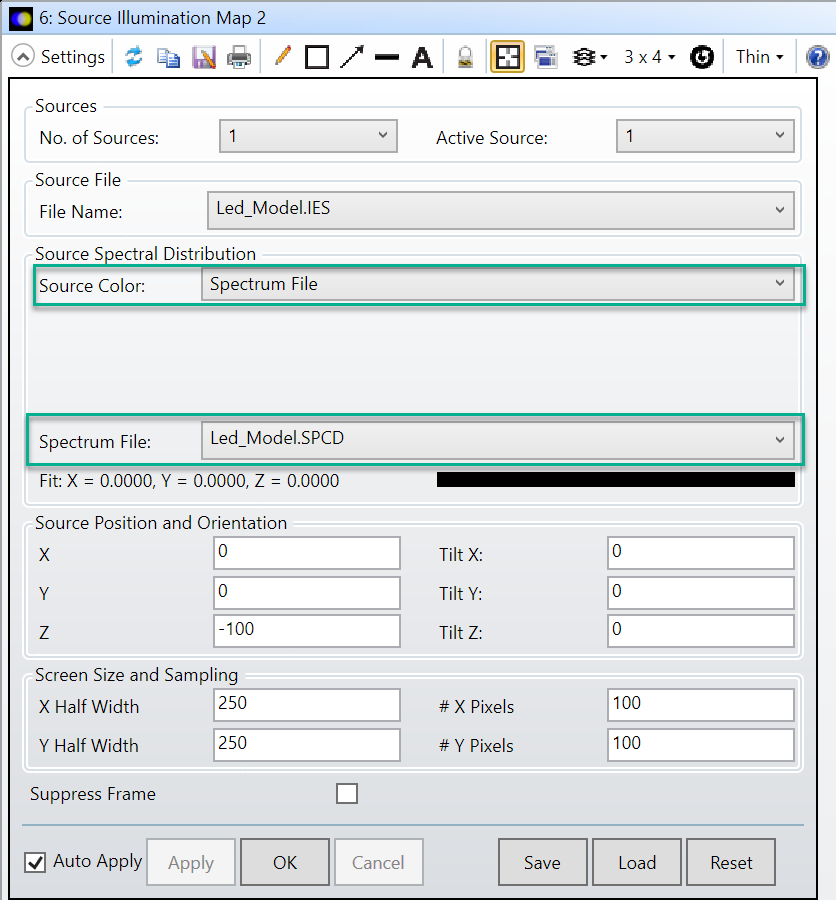
但是,在示例中,光源只发射两种波长(0.46和0.57微米)的光,并且具有相同的权重(可以通过在任何文本编辑器(例如:记事本)中手动打开SPCD文件确认)。因此,光谱文件不能用于OpticStudio,因为它包含的点太少(SPCD文件中最少的波长数为3)。因此,在这种情况下,最简单的方法是在波长数据 ( Wavelength Data ) 对话框中定义适当的波长,并选择:光源颜色 ( Source Color ):系统波长 ( System Wavelengths )。
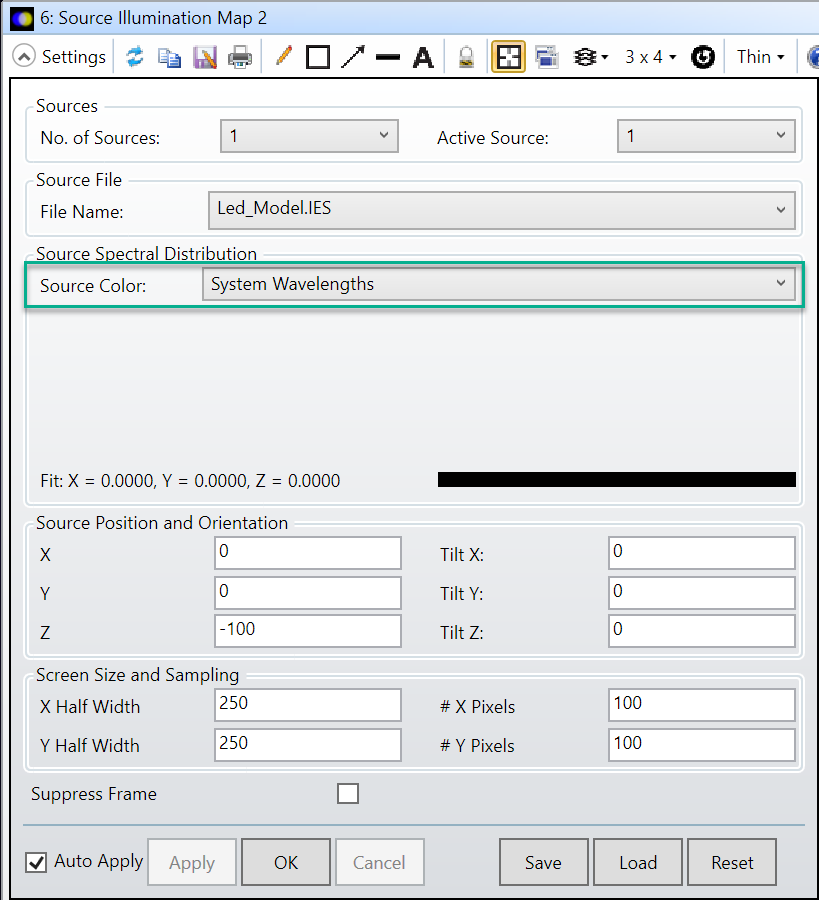
使用上图显示的光源位置和方向 ( Source Position and Orientation ) 以及屏幕大小和采样 ( Screen Size and Sampling )设置,SDF和IES文件的运行结果如下:
SDF
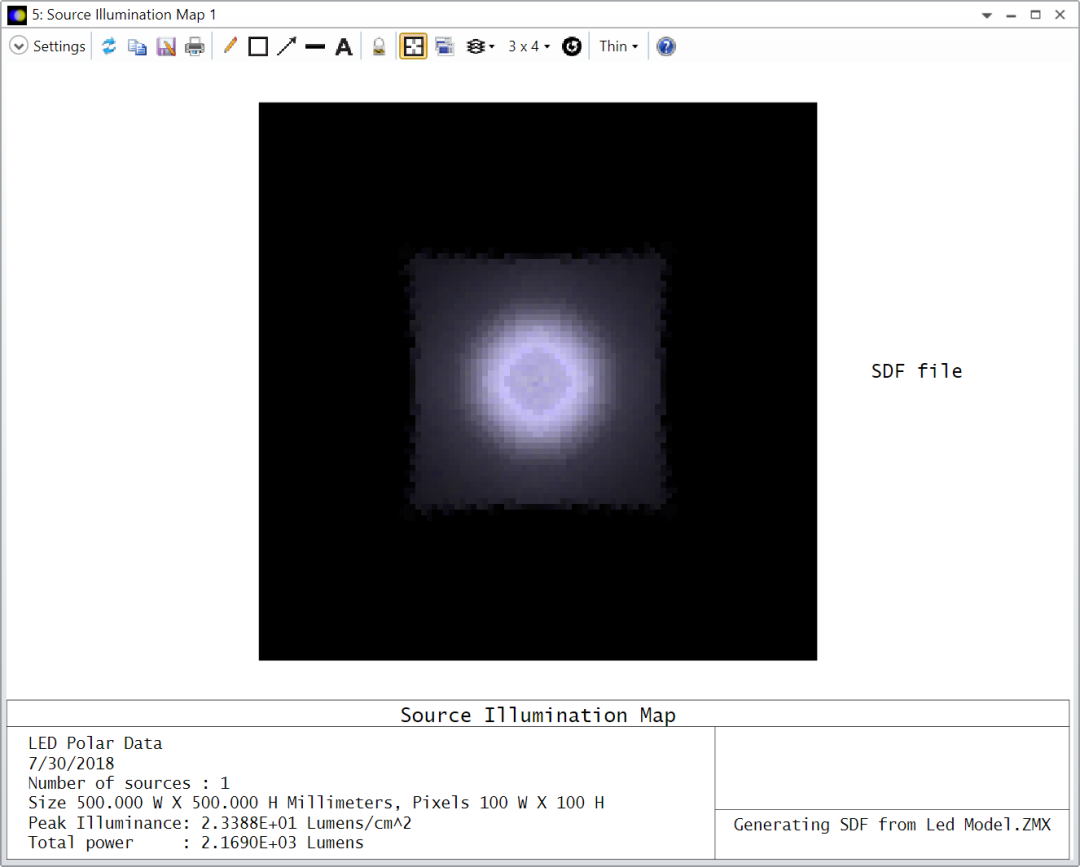
IES
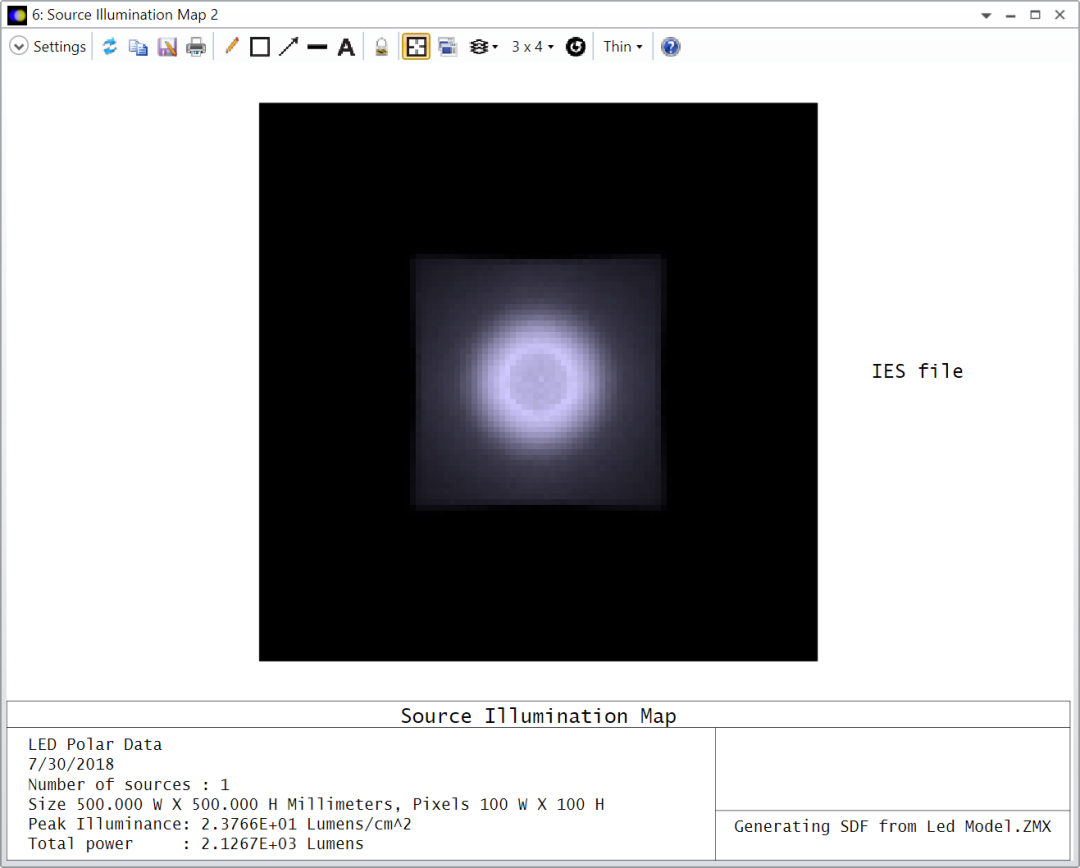
这两种情况再次具有很好的一致性,IES数据在这种情况下显示出更平滑的结果。
如果希望在光学系统中使用生成的IES文件,则可以在非序列系统中选择IESNA文件光源物体,并选择所需的IES文件作为输入。为了正确地建模光源的光谱分布,通常还需要在“物体属性 ( Object Properties )”对话框的“光源”选项卡中将光源颜色设置为“光谱文件(Spectrum File)”,并指定从SDF转换为IES时创建的相应SPCD文件。同样,这种操作对于光源只包含两个具有相同权重的特定波长的文件是没有必要的,因为,这些信息可以直接从系统的波长数据对话框中得到。
